Korea Regional Forum of the Passwordless Alliance
Overseas Entrusted Logins Shake Digital Sovereignty!
Recently, not only the EU but the entire world is paying attention to Sovereign AI. The national strategy to develop artificial intelligence (AI) independently without relying on foreign big tech companies and to utilize data is being promoted as an important direction for digital sovereignty.
However, I believe that a field that is just as urgent and should be considered together as Sovereign AI is ‘Sovereign Login.’
Most users store their IDs and passwords in the web browser when using online services, then use the password autofill function later, or log in to other online services using social logins from foreign companies such as Google, Facebook, MS, and Apple. In addition, major overseas online services are actively promoting passwordless login through biometric-based passkeys.
However, browser autofill, social logins, and biometric passkeys used for login convenience all result in digital keys that should only be known to the user being managed overseas. Browser autofill uses the password manager function of the browser developer, where all user IDs and passwords are synchronized to foreign servers. Social login is a structure in which a foreign operator is authorized to perform authentication between service users and providers. Finally, biometric passkeys are also synchronized with foreign platform operators who developed the OS, meaning biometric private keys are managed by foreign companies.
In short, the keys that can access all online data and activity, including privacy, are stored by foreign companies. Even if a domestic user uses a domestic service, if the digital key is entrusted overseas, it means not only the user has access to all data and activity. If we continue to entrust digital keys to third parties without thought for convenience, the user’s digital sovereignty has already disappeared. This is not a simple matter of technical choice but a fundamental problem in which the structure entrusts online identity and information sovereignty to foreign entities. At a time when the word ‘sovereign’ is being circulated through AI, it is time to fundamentally consider and practice ‘Sovereign Login’ for securing digital sovereignty.
However, I believe that a field that is just as urgent and should be considered together as Sovereign AI is ‘Sovereign Login.’
Most users store their IDs and passwords in the web browser when using online services, then use the password autofill function later, or log in to other online services using social logins from foreign companies such as Google, Facebook, MS, and Apple. In addition, major overseas online services are actively promoting passwordless login through biometric-based passkeys.
However, browser autofill, social logins, and biometric passkeys used for login convenience all result in digital keys that should only be known to the user being managed overseas. Browser autofill uses the password manager function of the browser developer, where all user IDs and passwords are synchronized to foreign servers. Social login is a structure in which a foreign operator is authorized to perform authentication between service users and providers. Finally, biometric passkeys are also synchronized with foreign platform operators who developed the OS, meaning biometric private keys are managed by foreign companies.
In short, the keys that can access all online data and activity, including privacy, are stored by foreign companies. Even if a domestic user uses a domestic service, if the digital key is entrusted overseas, it means not only the user has access to all data and activity. If we continue to entrust digital keys to third parties without thought for convenience, the user’s digital sovereignty has already disappeared. This is not a simple matter of technical choice but a fundamental problem in which the structure entrusts online identity and information sovereignty to foreign entities. At a time when the word ‘sovereign’ is being circulated through AI, it is time to fundamentally consider and practice ‘Sovereign Login’ for securing digital sovereignty.
International Standards and Free Technologies to Solve Sovereign Login
Technologies that allow users to maintain convenience while not relying on third parties are emerging. Representative examples are the sovereign passwordless technology ‘Passwordless X1280’ and the sovereign password manager technology ‘QR Password Manager.’
Sovereign Passwordless Technology: Passwordless X1280
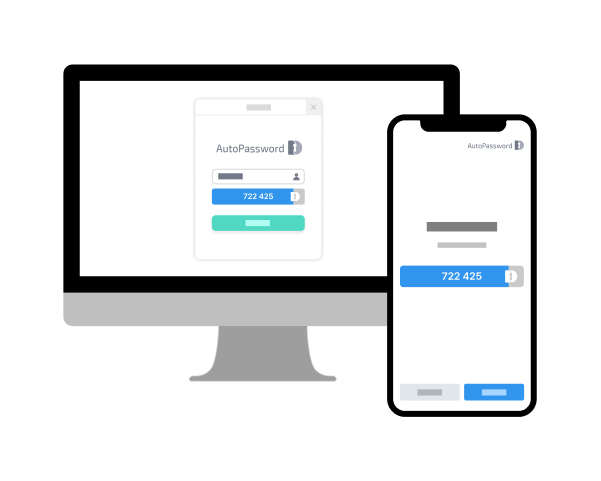
Passwordless X1280 is a method in which, when logging into an online service, the user does not enter a password, but the online service first presents an automatic password to the user, and the user approves it by comparing it with the value generated on their smartphone. In the conventional method, the user entered the password and the online service approved the match, but this technology allows the online service to present the automatic password, and the user approves the match on the smartphone, thereby eliminating the responsibility for the user to memorize or change the password.
In particular, it improves the unfair user responsibility structure where the service does not bear any responsibility even in cases of account theft or phishing, and only the user is held accountable due to poor management. It is a service responsibility model with fundamental phishing resistance, especially in situations where AI-based phishing attacks targeting users are increasing.
Furthermore, since the service presents a new automatic password every time it is accessed, users do not need to remember or manage different passwords for each service, allowing convenient access to various services. Unlike social login, there is no need to expose where the user visited to a third party.
This technology has been adopted as the international standard X.1280 by ITU, a UN-affiliated international technical standardization body, and is already being used in banks and government agencies. The non-profit Passwordless Alliance established in Geneva, Switzerland (www.passwordlessalliance.org) provides the software and training for free worldwide.
In particular, it improves the unfair user responsibility structure where the service does not bear any responsibility even in cases of account theft or phishing, and only the user is held accountable due to poor management. It is a service responsibility model with fundamental phishing resistance, especially in situations where AI-based phishing attacks targeting users are increasing.
Furthermore, since the service presents a new automatic password every time it is accessed, users do not need to remember or manage different passwords for each service, allowing convenient access to various services. Unlike social login, there is no need to expose where the user visited to a third party.
This technology has been adopted as the international standard X.1280 by ITU, a UN-affiliated international technical standardization body, and is already being used in banks and government agencies. The non-profit Passwordless Alliance established in Geneva, Switzerland (www.passwordlessalliance.org) provides the software and training for free worldwide.
Passwordless X1280 Login Screen
Sovereign Password Manager Technology: QR Password Manager
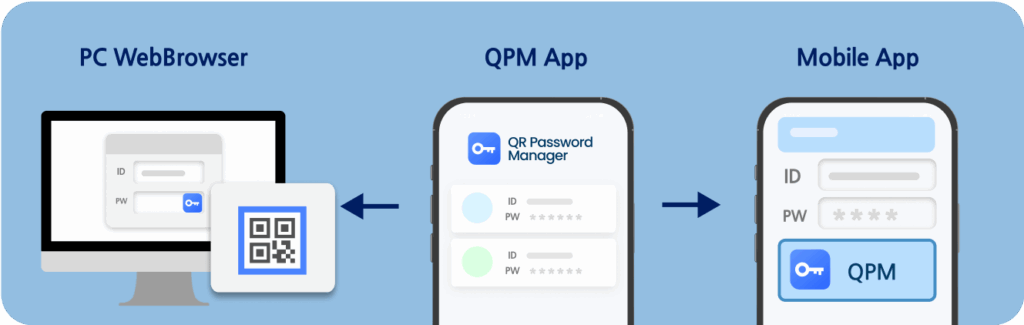
QR Password Manager (www.qrpasswordmanager.com) is a decentralized password manager that, unlike existing password managers that synchronize user IDs and passwords to a server, does not have a centralized synchronization server. All user IDs and passwords are encrypted and stored on the smartphone, and when login information is needed, they are automatically entered into another device through QR code-based communication.
The account information stored on the smartphone is kept in the secure area of the phone and is only transmitted through mobile biometric authentication.
QR Password Manager is personal software that anyone can use immediately by installing the QR Password Manager app on their smartphone and the QR Password Manager extension on their PC browser.
The account information stored on the smartphone is kept in the secure area of the phone and is only transmitted through mobile biometric authentication.
QR Password Manager is personal software that anyone can use immediately by installing the QR Password Manager app on their smartphone and the QR Password Manager extension on their PC browser.
QR Password Manager Login Screen
Sovereign Login Must Come First to Protect Sovereign AI
Before the grand discourse of Sovereign AI, the login, which is the starting point of digital activity, must be independent from foreign-dependent structures to truly secure digital sovereignty. Existing password autofill, social login, and biometric authentication methods lead to a third-party-dependent login structure. Within this structure, no matter what AI is used, our data can still be accessed by third parties.
Therefore, governments, companies, and users must make efforts to actively adopt and utilize sovereign login technologies that can strengthen their digital sovereignty from now on. If we remain stuck in familiar login methods distributed by foreign companies, we cannot recover true digital sovereignty.
Since free technologies and international standards related to sovereign login have already been developed, the government must support the dissemination and expansion of sovereign login systems established as international standards through policy, and promptly promote awareness improvement and institutional reform to convert the foreign-dependent login structure into an independent login structure.
In addition, online services should move away from the social login structure that shifts the burden of proof for login to the user, and participate in the use of free international standard technologies in which the online service bears the burden of proof and provides both convenience and safety to users.
Lastly, we urge general users to become independent in password management by using sovereign password manager technologies that adhere to the principle of not sharing passwords or biometric private keys with anyone, including browser or OS developers.
As Sovereign AI becomes a popular topic and thoughts about digital sovereignty begin to grow, now is the time to consider and practice the often-overlooked concept of Sovereign Login.
When Government, Companies, and Citizens All Practice ‘Sovereign Login’ Only when governments, companies, and citizens all practice the small principle of ‘Sovereign Login’ can the foundation of digital sovereignty be established.
Therefore, governments, companies, and users must make efforts to actively adopt and utilize sovereign login technologies that can strengthen their digital sovereignty from now on. If we remain stuck in familiar login methods distributed by foreign companies, we cannot recover true digital sovereignty.
Since free technologies and international standards related to sovereign login have already been developed, the government must support the dissemination and expansion of sovereign login systems established as international standards through policy, and promptly promote awareness improvement and institutional reform to convert the foreign-dependent login structure into an independent login structure.
In addition, online services should move away from the social login structure that shifts the burden of proof for login to the user, and participate in the use of free international standard technologies in which the online service bears the burden of proof and provides both convenience and safety to users.
Lastly, we urge general users to become independent in password management by using sovereign password manager technologies that adhere to the principle of not sharing passwords or biometric private keys with anyone, including browser or OS developers.
As Sovereign AI becomes a popular topic and thoughts about digital sovereignty begin to grow, now is the time to consider and practice the often-overlooked concept of Sovereign Login.
When Government, Companies, and Citizens All Practice ‘Sovereign Login’ Only when governments, companies, and citizens all practice the small principle of ‘Sovereign Login’ can the foundation of digital sovereignty be established.
Introduction to Korea Passwordless Alliance Forum
The Korea Passwordless Alliance Forum is a regional technical forum under the Passwordless Alliance, where Korea experts from industry, academia, and research institutes participate to promote and expand the adoption of passwordless technology in B2C online services.
This forum is operated under the Personal Information Protection Association with the support of TTA (Telecommunications Technology Association).
This forum is operated under the Personal Information Protection Association with the support of TTA (Telecommunications Technology Association).
